
COMMUNICATIONS IN NONCONVENTIONAL WARFARE
BACKGROUND
Many proponents of nuclear weapons have now come to acknowledge the fallacy of the position that nuclear confrontation or its threat can ultimately benefit any nation in international relations. To the contrary, it is being acknowledged by major world powers that reliance on nuclear weapons can ultimately result only in the horrors associated with a nuclear holocaust, without redeeming benefit or any winner. Both associated with and symbolized by this recognition, non-proliferation and disarmament agreements offer potential for a cessation of the nuclear arms race which began over fifty years ago. In contrast to nuclear warfare, representing the most violence achievable or imaginable, military defense strategists and tacticians now anticipate less violent (or lowered intensity) conflicts. Actually the evolution of low intensity conflicts (LIC), involving increasing risks to U.S. interests, can be traced as far back as the post World War II years, when the nuclear arms race was -born. Perhaps to be expected, as the threat of nuclear war appears to have subsided during this decade, a proliferation of regional conflicts and frequently localized terrorist-related crises has occurred. These conflicts often involve revolutions or insurgency movements in third world countries. They have increased partly as a result of two prominent global trends in political instability. First, the dissolution of empires in the western hemisphere, through disbanding colonial territories and, second, a concerted effort by former east-bloc communist and other third world countries to expand their areas of influence, with the stated aim of attaining increased power on the global stage.
NONCONVENTIONAL WARFARE
Recently, less violent nonconventional conflict has become the type most expected by our national defense and civil agencies. Now we even have an Assistant Secretary of Defense for Special Operations and LIC in the Department of Defense (DoD), a special unified Command for special operations and a special national funding program category to finance them. Congress has frequently urged the White House focus on LIC.
Types of nonconventional warfare are difficult to characterize, in that they vary considerably, are sporadic (often unpredictable) and elusive in form and scope, and usually involve civil as well as military participants. Thus, effective responses to pursue and defend our national interests and security require special adaptive and flexible warfare capabilities. Among these are critically required integrated military and civilian information systems.
Nonconventional conflicts by definition involve special techniques and resources. These are not conventional wars of the type traditionally encountered. They involve and often accentuate the unusual and unexpected. A principal characteristic is the frequently significant focus away from military combat to the political or social realm of a country's entire cultural environment. As stated earlier, their orientation often involves revolution or counter-revolution in a third world country, as described by Sam Sarkensian.
"Unconventional conflicts are political-military struggles involving two or more groups ruled by the indigenous elite for the purpose of taking control of the existing system without resorting to war in the traditional sense. These are struggles violently contesting control of the indigenous political-social system and are framed primarily in political-psychological terms rooted deeply in the indigenous culture. Such struggles, more often than not, are contested in a no-holds-barred environment, usually taking place in third world areas."
Thus, nonconventional warfare often must be fought coherently across the cultural spectrum to include political, economic, psychological and military confrontations.
To simplify terminology in this discussion, we will categorize nonconventional warfare as of two principal types, though it is certain some will not agree with the categorization.
The historically familiar one is the principally military activity involving an immediate tactical objective.
Special Operations - based on conventional military warfare methods but usually of short duration and "surgically" executed by specially trained and equipped personnel. Some examples are these:Direct Actions
Hit and Run
Sabotage
Hostage Interdiction or Rescue
Counterterrorism
Intelligence Collection/Surveillance/Reconnaissance
At least six military specialties have evolved to provide the various functions required for special operations in nonconventional warfare. Those are civil affairs, psychological operations, special forces, rangers, special aviation and sea-air-land (SEAL) specialists. The U.S. Marine Corps has established Marine Expeditionary Units with special capabilities when assigned special operations missions such as those listed at Table 1.

The other major category of nonconventional warfare is generally referred to as
Low Intensity Conflict (LIC). LIC is usually perceived as of longer duration and expanded scope than special operations. A LIC sometimes encompasses several individual special operations and is often more complex as well as being politically and socially focused. Also, it is most frequently revolution or counter-revolution oriented, involving a mix of military and civilian actions sometimes orchestrated by unfriendly outside governments or political groups. Direct armed U.S. intervention usually does not occur and a third country is sometimes engaged to assist as agent for U.S. interests. Some examples of LIC threats are listed at Table 2. Though one must be careful in generalizing about LIC, the term should be interpreted as meaning, at a minimum, something short of sustained conflict between conventional forces of two nations. U.S. Army Field Circular 100-20, Low Intensity Conflict, defines it as follows:"A limited political-military struggle to achieve political, military, social, economic and psychological objectives. It is often protracted and ranges from diplomatic, economic and psychological pressures through terrorism to insurgent war ... LIC is generally characterized by constraints of the geographic area, weaponry, tactics and level of violence."

Sub-categories of LIC support roles can be cautiously generalized, as in Table 3, but additional categories such as counter-narcotics or drug-interdiction activities can and should be recognized. The coordinated involvement of several governmental agencies beyond the DoD is essential in many nonconventional warfare operations. Thus, a coherent program supported by the highest governmental authority is necessary to establish nonconventional warfare policies, strategies, concepts and doctrine. Thus, an inter-agency plan is required to define individual agency missions, procedures and coordinating mechanisms (including communications systems). LIC incidents frequently occur unexpectedly; therefore, to respond effectively to situations threatening U.S. interests, rapid and synchronized activities are necessary in early stages to attain satisfactory results. The earlier assistance occurs, the more likely the conflict will be kept at lower levels of violence. For an adequately responsive worldwide, joint/allied coalition/inter-agency contingency plan to be established, coordinated regional threat measures must be agreed to in advance to trigger actions defined in the plan. Of equal importance is a reliable, flexible, adaptable and interoperable communications architecture established to execute such a plan whenever and wherever the conflict occurs.
INTELLIGENCE, SURVEILLANCE AND RECONNAISSANCE REQUIREMENTS
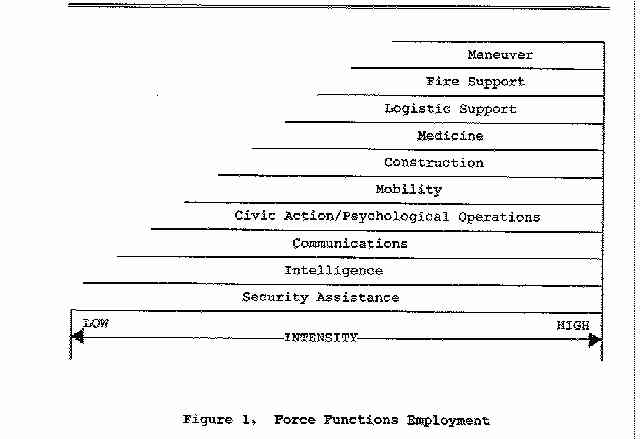
Levels of effectiveness of various nonconventional warfare functions vary with the level of conflict intensity (violence level), as indicated by Figure 1. It is apparent that intelligence, surveillance and reconnaissance are most effective in less violent stages of conflict. This is true in counterinsurgency and counterterrorism incidents and, even more so, in insurgencies where intelligence, surveillance and reconnaissance resources are applied before combat forces. But, even in more intense stages of conflict, military intelligence, surveillance and reconnaissance are significant force multipliers capable of increasing the effectiveness of forces supported. Thus, the earliest assistance to our allies in training them the importance and techniques for applying military intelligence, surveillance and reconnaissance is extremely important.
Due to the typically rapid escalation of violence in conflicts in unstable third world areas, necessary intelligence support is frequently not adequately available in these critical less violent stages. Often, military intelligence units are not able to acquire all the information needed before civilian and military special operations teams must be deployed. And subsequently, though the general level of available intelligence information may increase, deficiencies continue in critically needed detailed information on target areas, terminal objectives, local sympathizers, friendly forces and adversary positions. Host-nations do not always have effective technical or military human intelligence (HUMINT) systems, themselves, to help significantly.
Also, depending upon the specific mission or operation, the appropriate types of intelligence and the approach to acquiring it varies. Each operation is distinct. Effective intelligence support requires both consideration of overall nonconventional warfare concepts and the specific type of mission or operation being undertaken. Neither concept of nonconventional warfare,
LIC or Special Operations should be generalized to a perception of a generic warfare type to be supported by intelligence. Any such generic perception cannot cover the full spectrum of nonconventional warfare but can contribute to a false sense of coherency and completeness in plans.Further, success can not be secured by attempting to shoehorn, categorize or manage nonconventional warfare as tactical or strategic. Such lines blur in these conflicts. An excellent example of this blurring of lines is the area of intelligence support, where information from what are usually termed "strategic" sources must be used for timely responses to "tactical" operations. Actually, intelligence, surveillance and reconnaissance support is frequently required from national "strategic" systems/sources to support both U.S. and host-nation operations. Timely signals intelligence (SIGINT) and imagery intelligence (IMINT) can be extremely effective in filling what has been called a "technical void" in information needed in third world insurgency conflicts. However, for the information to be provided where and when needed in the form needed, a carefully planned, flexible, adaptive information exchange system is needed. Such a system must respond rapidly wherever needed and be deployable in a modular fashion, to meet the mission at hand, with standard interfaces capable of connecting as many information transport media as possible to as many telecommunications systems as possible in all the far flung regions. Furthermore, national agencies involved in the collection, processing and dissemination of critically needed information must accept responsibility for responsively providing it to the operating units at the other end of those telecommunications systems, rather than closely guarding it, according to rules and procedures established for long-term conventional warfare strategies.
Nevertheless, no matter how efficient the information infrastructure provided, to be effective, military intelligence, surveillance and reconnaissance personnel must be specially prepared to manage the acquisition, analysis and dissemination of the appropriate information in a format useable by the operational commander (U.S. or host-nation). In nonconventional warfare, intelligence officers need a thorough understanding of general intelligence principles and conventional intelligence methods in order to innovatively adapt them to fit specific nonconventional warfare operations. For example, no matter what the operation, some type of intelligence preparation of the battlefield (IPB) is necessary. This requires that the intelligence officer innovatively adapt conventional IPB procedures to delineate and clarify the threat applicable to the mission at hand. He or she must exhaustively collect, analyze and document all obtainable information on the objective, timeframes involved, the adversary, the terrain and weather forecasts. Then, he must further correlate that with detailed data on allied units and/or friendly forces. Besides requesting data from local or regional sources, he or she must know where to obtain information from national collectors and data bases on installations and personalities, before finally integrating all available data for an all source threat assessment, with indications and warning (I&W) measures of adversary intentions and target locations.
Certainly intelligence is important in all warfare, but it is critical in nonconventional warfare operations (especially their less violent stages); thus, the intelligence officer must prudently assess information sources available and their products' timeliness, utility value, dependability and limitations. That officer must also recognize the importance of communications systems and services to achieve an appropriate balance of information from sources of all types, both organic and from higher echelons. Sources can generally be categorized as either HUMINT or Technical. Ideally the intelligence officer is able to key requirements from one source by information derived from another. As was recently made clear by former MGen John F. Stewart, USA, this most effectively applies the resources available (including information systems):
"All intelligence means must be used in LIC. Cross-cueing of systems and assets, both within and among disciplines is especially critical to LIC where sources are hidden, indicators are subtle and resources are scarce."
Information from technical collectors is usually more perishable and must be more closely managed. These include IMINT, RADAR, and SIGINT. Usually the higher the echelon of the collector, the slower the receipt and associated value in operational application. RADAR is often of limited use in nonconventional warfare land operations due to limitations in distinguishing between civilians and adversaries. Similar difficulties arise with other technical sources; thus, all-source information analysis is essential for a completely reliable picture. Particularly in counter insurgency or foreign internal defense (FID) missions, no single source is 100% reliable. Each must be corroborated, especially where civilians and insurgents are intermingled. Further coordination and comparisons are also advisable or necessary with host-nation intelligence elements through national, regional or provincial intelligence coordination centers.
HUMINT's value is frequently emphasized in unconventional warfare, especially in early stages of a counterinsurgency LIC. This is partly due to the importance of distinguishing between adversaries and civilians. HUMINT collection activities include interrogation of prisoners and civilians, sometimes with polygraphs, observing troop movements, exploitation of mass media and document searches. Patrols and guard posts can also contribute additional useful data. HUMINT may be collected more slowly than that of the technical systems, but (depending upon source reliability) the information gained is regarded as more accurate and less transitory, requiring less frequent updating/refreshing. There is a sometimes tendency to become overwhelmed with impressive technology in both collection and analysis, but it should not be allowed to divert resources and recognition from valuable HUMINT skills badly needed in nonconventional warfare.
SIGINT's sometimes-lower emphasis in nonconventional warfare results partly from the following. In the earlier stages of LIC incidents, adversaries are less well organized and frequently do not use uniform communications procedures and standard equipment. In these stages there also is little data on their electronic systems. Further, they frequently use diverse models of commercial off-the-shelf equipment (sometimes more effective in avoiding detection and intercept due to modern sophisticated signal processing components). However, in later stages of conflict, the value of SIGINT increases as organization improves, requiring more standardized communications equipment and procedures, and as more extensive data bases are established on electronic systems being used.
The second principal technical source is imagery intelligence (IMINT), mostly photographic intelligence (PHOTINT), which provides excellent data base information on the terrain, facilities and movements to support nonconventional missions. However, unless analysts are sharp, imagery products may not be received timely enough for day-to-day operational applications
Besides HUMINT, SIGINT and IMINT from U.S. national (strategic) sources, the intelligence officer can request theater and host-nation operational units to collect information. In doing so and in managing collection tasking, he or she must keep in mind that the higher the echelon of the collector, the more sophisticated the information infrastructure required or the slower the receipt of the information. In some cases, the information available may exceed the capacity of available telecommunications media to bring it to the scene, requiring summarization reports or coding of data. These factors must be weighed against the value and dependability of alternative/complementary sources. Besides dedicated HUMINT missions and patrols, other U.S. and host-nation intelligence, surveillance and reconnaissance assets which can be information sources include unmanned aerial vehicles (UAV), remotely emplaceable sensors (REMS), listening and observation posts, fire support teams, overflights, artillery and air defense radars and engineering operations.
A very important early intelligence function is to develop I&W identifiers useful in triggering maneuvers or operations and identifying/locating targets for those operations. This requires identifier templating methodologies that can be effectively applied rapidly to specific scenarios to highlight trouble spots and potential targets. These can be used as effective aids in nonconventional warfare operations to track indicators of insurgent activity and be useful in triggering appropriate responses to counter that activity.
As was stated earlier, other than coping with the special requirements for IPB, setting up an intelligence collection management approach, establishing I&W identifiers and pointing out potential targets, - few generalizations can be made about intelligence, surveillance and reconnaissance support necessary for the wide range of special missions and functions associated with nonconventional warfare. Some of the principal ones are briefly discussed below, but it is important to keep in mind that they do not usually take place alone. Rather, they are conducted in concert or (in some cases without the awareness of all operators) covertly overlap.
Security Assistance
. Usually the principal U.S. military function in LIC, "security assistance" is ill defined and fraught with political sensitivities. Thus, how it is applied to a specific conflict varies significantly. Certainly, at a minimum, it includes some level of training of indigenous combatants and providing them necessary resources, including weapons, sometimes through a third-nation agent. As was emphasized by MGen Stewart, the earliest possible training of host-nation forces in effective military intelligence is extremely important and potentially effective in reducing the level of, perhaps more expensive, assistance later.Foreign Internal Defense
(FID). FID usually involves a total national struggle of a third world nation, encompassing conventional armed conflict as well as economic and psychological warfare and terrorism and insurgency. These situations typically include a mixture of military, political and social warfare, often associated with an international political struggle.Psychological Operations
(PSYOPS). PSYOPS missions are special operations with the objective of influencing behavior, usually without violence, or occasionally augmenting violent actions, of not only the adversaries, military components, but also his non-belligerent allies and the indigenous population (and sometimes the U.S. and world population). Among other means, these missions use various media for spreading propaganda. The control of the press and other mass media is one mechanism. This can be accomplished by friendly persuasion by public affairs officers (PAO) to influence reporters or can go the extreme of physically or electronically overriding public radio broadcasts. Other tools of PSYOP may include information electronic warfare, electronic jamming and deception. PSYOP is very effective in counterinsurgency and counterterrorism, but timing is critical - one of the most critical for success. PSYOP activity must be synchronized with the state of affairs perceived by the adversary, and the populace, thus it must be coordinated and synchronized with other operations (requiring dependable responsive communications).Special Missions
. These include a variety of worldwide special operations, such as rescue, sabotage, reconnaissance and intelligence collection. Personnel assigned to such operations require special abilities and need special equipment. An example of a special force is a SIGINT team. This team requires small lightweight, ruggedized and frequently waterproof communications equipment with special characteristics if the mission takes place in denied, enemy-controlled areas. Such a communications system should operate with low power and in a low probability of intercept/detection (LPI/LPD) manner. The radio "fingerprint" or waveform of the system should also be crafted to avoid identifying the mission by its unique characteristics. Operators assigned to SIGINT teams must have special abilities in intercepting the adversary communications (voice and manual morse code principally), radio direction finding (geolocation), analysis of communications traffic and, occasionally, in information warfare techniques such as electronic jamming and deception. Another example is a special aviation unit conducting airmobile operations of a wide range of potential types. Some examples of these are information warfare, rescue, SIGINT and RADAR imagery collection and targeting. Intelligence, surveillance and reconnaissance information obtained in tactical airmobile operations is sometimes downlinked directly over radio circuits to intelligence centers for all-source intelligence updates. Again, the operators assigned to these missions need special technical abilities, special equipment and tradecraft.Civil Affairs
. Reserve forces frequently perform this critical role in many LIC situations with special expertise in civil administration. Civil affairs should and often is closely coordinated with PSYOPS activity. The civil affairs officer's principal objectives are to mobilize public (civilian) support for the legitimate political control entities and procedures. This political legitimacy must be perceived not only by the indigenous populace, but also by Americans and important international bodies. The reason for the importance of its close tie with PSYOP is apparent. Civil affairs missions supporting FID, as well as supporting resistance forces in insurgencies, involve people, ideas, ideals, hopes, frustrations and expectations. People (civilians and military) are the key to success; therefore, the success of military actions must be interpreted by their impact on the indigenous population, though the effect of combat is certainly relevant. Success in these endeavors requires timely information exchange among military and civilian units or organizations, both within the host-nation and with the outside world. Military commanders and civil authorities/agencies must be able to send requests and reports to higher authorities and to each other while receiving responses, rapidlyCounter-Narcotics/Drug-Interdiction
. These operations are assigned top-level priority on the national agenda and involve international cooperative activities of civil and military agencies requiring the support and oversight of the highest authorities of those nations as well. Intelligence, timing and communications are key elements to success. All the intelligence, surveillance and reconnaissance disciplines and methodologies discussed above relative to other nonconventional warfare operations apply to these. Their application, however, are even more complex, due to the rapidly changing techniques and approaches of the illegal drug cartels (the adversaries). Worldwide information from all sources must be rapidly collected in a coordinated near-real-time manner, evaluated in international /inter-agency coordination centers and disseminated to international/inter-agency force elements over secure communications systems. The adversary is assumed to be well equipped with the latest sophisticated high technology to detect and intercept interdiction force communications and locate important force locations. It is, therefore, very important to not allow adversary knowledge of our critical intelligence, surveillance and reconnaissance information collection, processing and dissemination system capabilities and techniques.COMMUNICATIONS REQUIREMENTS
It is apparent that to present a complete description of the necessary flow of information (even solely intelligence, surveillance and reconnaissance information) among participants in nonconventional warfare (of all types) would, if not impossible, certainly be beyond the scope of this essay. An adequate description should include a multi-dimensional matrix of, at a minimum, (1) all the potentially unstable third world nations, (2) the intelligence disciplines (HUMINT, SIGINT, IMINT and some others), (3) all types of missions to be supported (for example security assistance, FID, PSYOP, civil affairs, drug interdiction and other special missions), and (4) the multitude of communications system configurations. Obviously a formidable task, even without including the variable of responsiveness in terms of time and political commitment. For example, particular communications systems could be set up over some period of time, yet not be available on short notice in low intensity stages of conflict, when intelligence, surveillance and reconnaissance can be so effective.
The intent here is to re-emphasize the danger in generalizing about certain communications techniques or systems as being the answer to special operations, LIC or nonconventional warfare requirements. Caution should be emphasized in such generalizations and only comprehensive coherent architectural perspectives should even be considered for evaluating generalizations of this type.
Communications systems intended for nonconventional warfare information exchange should be designed carefully to satisfy the particular requirements of a set of special missions, functions or operations; (Such as the 3 Set Model described by MGen Stewart.); though, as stated above, missions, operations and functions do not often take place alone (in a vacuum), but frequently overlap and complement each other. Nevertheless, some general communications system performance requirements, by mission area, are briefly discussed below and summarized together in a list at Table 3.
Security Assistance
. Here, mostly for training missions, the need for communications systems, which are interoperable with those of conventional forces of all military services, host-nation and third-party nations, is most prominent. Security assistance teams must be equipped to-obtain information from U.S. as well as host and third party national and tactical sources. Secure coordination network capabilities, as well as point-to-point links are usually necessary. Secure data connectivity to U.S. national databases is useful in contributing to the development of I&W identifiers. Thus, both voice and data is required, but frequently only voice can be compatibly exchanged with participating foreign units (military and/or civilian). Generally, communications systems used by U.S. participants will be driven by those available to those being assisted, or be compatible with them.Foreign Internal Defense
(FID). A more extensive communications infrastructure is required in these situations to obtain, correlate and disseminate intelligence information among multiple sources and operational elements. Very sophisticated information collection processing and exchange systems are needed. Information of all types must be exchanged among diverse and geographically distributed host-nation and U.S. units as well as among regional facilities. The required infrastructure includes integrated transmission capabilities for (formal written) message, data, imagery and voice networks. Though host-nation and regional third-party forces must be interconnected to certain systems, they need not/should not be connected to them all. Besides the technologically sophisticated information infrastructure that may be developed for these joint international operations, it must be acknowledged - and remembered by system integrators that frequently special missions are underway which require covert communications capabilities. For example, special forces and drug-interdiction teams may be operating in terrain controlled by adversaries but require communications interfaces to support and coordinate with other operational units. Those communications must use systems that exhibit LPI/LPD characteristics. Another important consideration is that, in its earlier stages, FID units may not be afforded the luxury of the sophisticated information infrastructure that may be installed over time. In preliminary stages, any type of reliable, rapidly deployable, secure communications system capable of connecting U.S. forces to critical U.S. national sources of information, to other participating U.S organizations and to local/regional host-nation forces is essential.Psychological Operations
(PSYOPS) - As stated earlier, the critical factor in PSYOPS is timing. Thus, critical intelligence and related operational information must be coordinated on a timely basis. This requires interoperable communications capabilities that can be rapidly and reliably established. Associated signal processing capabilities useful in information warfare, jamming and deception across wide segments of the spectrum are also useful in supporting PSYOPS activities. Inasmuch as PSYOPS missions may be pursued in forbidden territory, covert communications system characteristics such as LPI/LPD may be required. It should also be emphasized that capitalizing on indigenous broadcast facilities for PSYOPS operations is an efficient approach, where appropriate.Special Missions
. These are conducted by a variety of specially trained and equipped forces. They all require special support, depending on the specific mission at hand. An example was discussed earlier for a SIGINT team. Only a few generalizations may be safely and usefully distilled.Relative to intelligence information support, it is important to remember that these forces are frequently engaged in surveillance, reconnaissance or intelligence collection activities in denied territory. Thus, their sensitivity to detection, interception and location through communications is critical to not only their success but their survival as well. They must, however, be provided information often derived from other sources for their verification. Also, they must report their observations, frequently critically important for I&W support to other operations and functions in the conflict.
Therefore, the emphasis is on reliable, small, lightweight, waterproof, simple to operate communications systems that do not give the mission away or get the team killed as a result of being detected, intercepted or located through radio direction finding. Usually the amount of information to be sent or received is small and can be coded to require only short transmissions with low power emissions.
Special teams in these categories also require special communications equipment useful in information warfare applications. Ideally the functions of that equipment should be integrated into the radios they use to communicate.
Civil Affairs
. Multiple communications media are essential in providing critical information to support civil affairs operations. Access to international communications media to exchange various types of information with U.S. national, host-nation, regional and international organizational units both in and out of the host-nation is required. Complementing this is the necessity of exchanging information with and among units engaged in covert activities, both civilian and military. Reports on principally HUMINT, but SIGINT and IMINT information as well, relating to the civil and military affairs regionally and internationally are important. As a general rule, covert activities must be directly and closely controlled from the highest authority within government, thus they require reliable secure communications to the appropriate offices. This information will normally, where possible, be correlated and analyzed at a central facility in the region, where it can be used with PSYOPS to strengthen and increase the credibility and efficiency of legitimate governmental functions, while increasing popular support. A regional or provincial civil coordination center is an appropriate hub for communications supporting civil affairs, with connections to fixed and mobile distant units operating in secure (encrypted) and clear (non-secure) modes, as appropriate for the particular support unit, within the region and outside (including the continental U.S. (CONUS)). Access to public media must be provided and ideally should be obtainable from the same equipment.Counter-narcotics/Drug-Interdiction
. This is another mission/operation type involving international and inter-agency coordinated activity, thus requiring adaptable, flexible and interoperable communications systems. A significant SIGINT threat from drug smuggling cartels is also assumed; thus, the communications must be secured and made resistant to detection and intercept. Information of many types from a myriad of sources must be securely exchanged with joint/allied/inter-agency correlation/coordination centers and disseminated to remote operating units, both overt and covert. Therefore, connectivity must be extensive and capable of being flexibly and adaptively extended virtually worldwide on a timely/responsive basis to cover contingencies in the various drug smuggling regions and allow access by a multitude of national and international organizational units and facilities, with varying security requirement levels. Thus, both link and network end-to-end communications security (COMSEC) and transmission security (TRANSEC) is needed. These security requirements must be added to those (called COMPUSEC) for the various computer/ automated systems involved in storing and processing the data. The responsiveness of this system must be rapid and adaptable to variations in loading while maintaining a high level of reliability, all due to the critical nature of timing in highly sophisticated/complex distributed operations. For example, frequently information from strategic national sensors must be sanitized, translated and disseminated to feed coordinated timely inter-agency/international tactical operations to interdict rapidly moving drug smuggling activities.With such a diverse set of critical information exchange requirements related to nonconventional warfare, obviously no one communication system can satisfy them all. However, to identify efficient and cost-effective (affordable) solutions, it is recommended that system planners and integrators attempt maximum exploitation of modern electronic signal processing technology in designing systems which can be configured modularly to be simple to operate but effectively support as many requirements as possible. To the extent that a relatively small number of modular subsystems can be integrated in this manner, the list at Table 4 contains some recommended general performance characteristics they should share or collectively provide.

EMERGING COMMUNICATIONS TECHNOLOGY
Many government and commercial satellite communications systems have capabilities included in the performance requirement list. For example, long-haul high frequency (HF) radio communications systems are widely available throughout the world and offer capabilities that complement line of sight (LOS) and satellite transmission services. In addition, very high frequency (VHF) communications systems, including meteor burst communications (MBC) offer special characteristics for missions in certain geographic regions and terrain and in some EW environments.
Products are available for each of the above media and others that contain the latest microprocessor controlled signal processing techniques and many are capable of being interconnected effectively. Therefore, it is recommended that systems being designed for these requirements be equipped to coherently operate in adaptive modular multimedia configurations.
Multimedia communications systems should be designed to provide the capability to adaptively switch from one transmission media to another through the same node, thereby providing the subscriber with substantial flexibility in the employment of various transmission systems. This type of adaptive modular architecture allows information to be sent over multiple paths connecting a set of nodes. Here the term node is intended to describe an end-user point, a relay point or a hub/switching center. The various transmission media over which information can be communicated long distances to connect those nodes are metallic and glass-fiber lines/cable and HF (including HF-Packet), VHF/MBC, terrestrial ultra high frequency (UHF) line of sight and satellites (including super high frequency (SHF) and extremely high frequency (EHF)) radio circuits. These media can be interconnected point-to-point to form single links or using relay nodes to form multilink networks with the opportunity/option of selecting appropriate transmission systems for each link and automatically/adaptively selecting the appropriate link at a particular time for a particular message. A multimedia system takes advantage of modern opportunities to efficiently and cost-effectively interconnect diverse communications assets. Over such systems, the capability usually exists to pass varying amounts of information between any set of nodes, with the capacity and speed of service depending on existing conditions. This is possible due to the significant reliability and survivability advantages of a richly connected adaptable multimedia architecture.
Requiring standard interfaces and procedures to provide compatibility and interoperability among potentially diverse systems and segments of systems using various transmission media is essential to interconnect multimedia systems. This interoperability must be transparent to the (usually non-communicator) operators and automated to the extent that it requires no trained operator intervention. Since certain transmission media have vastly different information transfer volume and speed of service capabilities, the highest volume, fastest and most capable systems must be able to automatically throttle-down and work with slower smaller throughput systems. Thus, multimedia systems must be designed with integral adaptability and flexibility.
Specific interoperability areas to be reckoned with are commonality or compatibility in addressing schemes, switching procedures and routing tables, subscriber end-user equipment, transmission media parameters (such as MODEMs, transceivers and signaling/modulation techniques), as well as COMSEC and TRANSEC algorithms and key management techniques.
As discussed above, modern technology is producing smaller, less expensive and secure communications products for all transmission media, many working as "hybrids" effectively across the electromagnetic spectrum. These new technologies include advanced systems which extend frequency spectrum boundaries, include linear broadband amplifiers, adaptive power management, microprocessor controlled frequency agile couplers, filters, synthesizers and antennas, as well as automatic code combining schemes to increase efficiency and throughput in all types of radio propagation or EW conditions. They also include capabilities to internally sample propagation conditions and information warfare activities, while automatically adapting certain parameters of the transmission system to perform more effectively under conditions or threats experienced, by changing data rates, frequencies, modulation schemes or power levels.
Certain of these modern communications capabilities are built into the equipment itself (hardware or firmware), including adaptive data and coding rates, spread spectrum modulation and time and frequency diversity. Others are created by innovative system design techniques, including multiple message injection points, flexible/adaptive architecture, adaptive frequency management and ground wave exploitation, to name a few.
Products can be bought off-the-shelf (and many times are by LIC adversaries) that offer very sophisticated but easy to operate services. Some examples that exist or are automatic link establishment, jam resistance, LPI/LPD complex interrelated algorithms, sophisticated integrated microprocessor controlled COMSEC and TRANSEC features, as well as media-hybrid performance capabilities (including HF/VHF/MBC combinations for example).
Products are emerging that operate in narrow and wideband modes. For example, thanks to modern VLSI/VHSIC components, startling performance parameters are being demonstrated with wideband spread spectrum HF radio using very low power and frequency excision techniques to avoid jamming and detection while accommodating interference. Such a system can apply differential phase shift keying (DPSK) to reliably provide high data rate throughputs over links hundreds of miles long with as little as power lower than that used for a desk lamp. And narrowband HF communications systems are being produced with automated communications processors which provide frequency-hopping as an option and spread spectrum modulation to adaptively send variable data rates. Also, automated processing modules are integrated into the system to send coded/synthesized voice messages.
Modern communications systems combine MODEM, controller and radio into one box to provide miniaturized handheld adaptive multi-spectral systems that are simple to operate. They include integral adaptive frequency management capabilities using automated sounding and predictive algorithms. These are especially adroit at performing in high threat information warfare environments with the capability of adaptively using multiple propagating media with the necessary capability to communicate with simpler systems with less sophisticated repertoires.
But, besides the jam resistance, LPI/LPD and survivability advantages available from advanced microprocessor controlled signal processing, many other advanced capabilities are now available to improve interoperability and connectivity to support nonconventional warfare communications requirements. Automated VLSI/VHSIC components can be programmed to automatically adapt to link or netted configurations, including supporting appropriate addressing schemes and security systems. For example, systems can be configured to support thousands of addressees geographically distributed across thousands of miles to provide multiple information transfer modes to broadcast (from space-based platforms) to all or selected subgroups of addressees to exchange all types of information (voice, data, video, etc.).
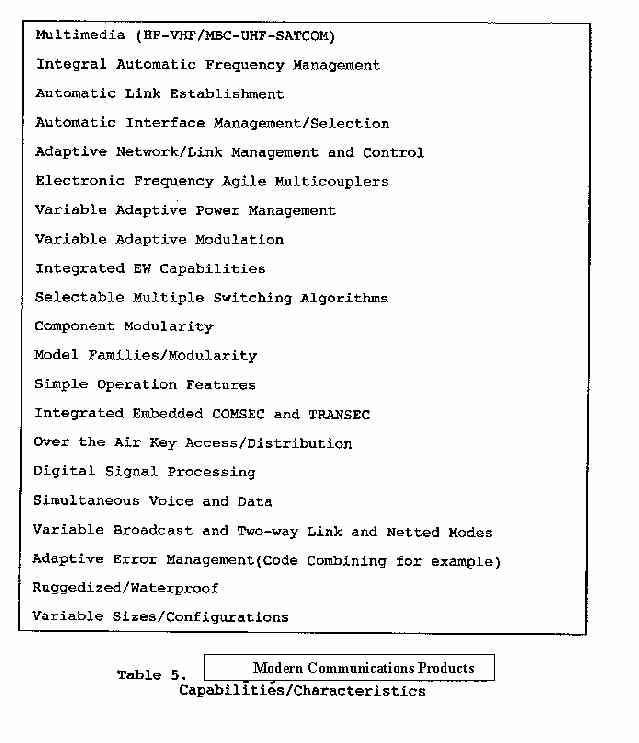
Table 5 is but a summary list of some advanced/adaptive communications performance capabilities now available.
WORLDWIDE NONCONVENTIONAL WARFARE CONTINGENCY COMMUNICATIONS SERVICES
The above discussion confirms a wide range of requirements to accommodate (1) the exchange of a variety of information types, (2) among varying numbers of subscribers, (3) at varying security levels, (4) at unpredictable locales around the world, (5) within unpredictable response timeframes, (6) in dramatically varying environments, and (7) with the necessity of adapting to available equipment, people and media. This supports the need for a coherent, flexible and adaptable communications service based on a modular information architecture to cost-effectively support these dynamic requirements as efficiently as possible and with as much simplicity as possible by exploiting the very efficient automated signal processing technology now available in the marketplace. An appropriate mix of available capabilities integrated as modular flexibly configurable sets of subsystems which operate in appropriate media to be assembled to meet the needs of the mission at hand is obviously the most logical approach and likely the most cost-effective over the long-term. For example, such an adaptive advanced multimedia architecture will allow the establishment of relatively richly connected telecommunications systems with minimal/manageable infrastructure on the scene in LIC scenarios when intelligence, surveillance and reconnaissance information can be most effective in reducing conflict intensity with the least violence.
One critically important component of this adaptable, rapidly configurable multimedia architecture is the establishment and maintenance of a basic, reliable and continuous worldwide HF radio coordination network. That network is the foundation upon which the more sophisticated and complex services and features of the system can be built and held together. That basic network element can be built upon a framework of cooperative agreements among joint and allied civil and military HF facility/system managers and is the baseline from which to rapidly establish more sophisticated links and networks at any time and to reliably re-establish contact if connectivity is disturbed. This coordination network will allow use of existing equipment of all countries. Another feature that should be included in the worldwide coordination network is a global broadcast mode, enabling subscribers everywhere to be easily and reliably contacted to pass the appropriate information or to establish a more extensive/secure link for information exchange.
Sources/References
Beans, BGEN James 0., "Marine Corps Intelligence in Low Intensity Conflicts," SIGNAL, March 1989, pp. 27-29.
Constantine, LTC Edward L., "Low Intensity Conflict: Are We Prepared"? Military Intelligence, June 1987, P. 39.
Levesque, Capt. Raymond W., "Counterinsurgency Intelligence," Military Intelligence, Oct-Dec 1986, P. 26.
Levesque, Capt. Raymond W., "LIC Doctrine and Intelligence, Military Intelligence, October 1987, pp. 32-34.
Peterson, Capt. William J.,"The Importance of PSYOPS and Intelligence in LIC," Military Intelligence, October 1987, P 31
Schemmer, Benjamin F., "Senate Leaders Ask Scowcroft for New White House Focus on Low-Intensity Conflict," Armed Forces Journal International, March 1989, pp. 66-67.
Stewart, MGen John F., "Military Intelligence Operations in Low-Intensity Conflict: An Organizational Model," Military Review, January 1988, pp. 18-27.
Sarkensian, Sam C., "The Myth of U.S. Capability in Unconventional Conflicts," Military Review, September 1988, pp 2-17.