
Today's Challenge - Managing Information Resources
A new management challenge has emerged for the federal government's national security enterprise. Information resources need more efficient and cost-effective management to exploit technology offering innovative information services enabling competitive advantages of "information superiority" and "dominance."
Information Dissemination Management
An Enabling Strategy
A White Paper by:
Ronald D. Elliott
22 August 1998
The Information Technology Revolution
As late as fifteen years ago automated information processing was being conducted in "glass houses" in centralized "mainframe" computer centers. Managing the information passing through such facilities was rather straightforward. However, information- processing technologies have changed dramatically in recent years.
First "personal" computers" (PCs) emerged that "stood alone" on desks of individual office-workers, then they were gradually interconnected to form "local area networks" (LANs) to enable share information as well as peripheral equipment and services.
Then, those LANs were interconnected with "wide-area networks" (WANs) to form concatenated grids forming worldwide ("global") networks, opening great opportunities for exchange and sharing of information and information services in powerful ways to enable synergistic opportunities inconceivable a few years ago, by most of us. We then took the PCs into our homes, to extend our work environment, and our "working hours" home environments.
Next, we connected databases across this new realm (to which someone applied the term "INTERNET"), enabling relational information processing offering greatly improved knowledge to achieve organizational goals. Then, with the arrival of "the web," we began interconnecting information storage and exchange services of even greater power in an even grander realm termed "CYBERSPACE." In only the past five years, we've begun "browsing" and "searching" and "gophering" through myriad information resources of our own organizations and those of others. In the latter part of this decade, we've even begun contemplating the placement of information processing itself on to the INTERNET by storing computer applications there for use by less powerful (and less expensive) personal computers. The apparent end-result is a "CYBERSPACE" containing infinite amounts of information and information processing services accessed through "windows" or "knowledge robots" that sit on our desks (and laps).
Impact to National Security Operations
The potential advantages offered to national security operations by these dynamically expanding technology-enabled tools and services are certainly revolutionary. The JOINT VISION 2010 goals and objectives of our Joint Staff acknowledge this. However, achieving the potential requires more attention and resources applied to managing information served up by those tools and services, because a counter-productive potential effect of the technology is to overwhelm those conducting operations with more information than they can cope with. Such an outcome can only further confuse decision-makers, not increase their knowledge and expedite their efforts, the ultimate objective.
Indicative of efforts currently directed at providing decision-makers more data rather than information contributing needed knowledge is the increasing number, type and capacity of telecommunications services being planned to support national security operations. Accelerating demand for telecommunications services (including larger volume capacity - called "bandwidth") frequently result in "stove-pipe" duplicative networks that restrict awareness of and access to information or require users to use duplicative systems. Uncoordinated (managed) responses to unbridled demands for such diverse telecommunications services will potentially result in overwhelming users with information they must sort through to obtain knowledge needed for effective efficient performance of assigned missions and functions.
What's needed is a new perspective on managing information resources to enable more cost-effective and efficient use of the technology to provide innovative and synergistic enterprise-wide information services offered by the technology to provide competitive advantages perceived by JOINT VISION 2010.
Therein lies the current challenge, addressed by this paper.
Enterprise-wide National Security Information Management
As postulated by JOINT VISION 2010, the emerging new millennium will be one where information, and the knowledge derived from it, becomes vital to the successful conduct of national security affairs of the federal government. Information is a critical integral resource of all national security activities. In the factory, the base or station, the headquarters, or at remote operational sites, information technology is the key to better decisions and timely implementation of those decisions across our national security enterprise.
In the evolving information age, the power of information is its potential multiplication effects on the value other resources. Individuals, organizations, industries and nations are seizing the opportunities offered by information management and information technology to become more competitive in the global environment by realizing and exploiting that potential. Therefore, information should be recognized as a core critical resource of the national security enterprise of our government, a resource requiring prudent and enlightened management to multiply the value and productivity of other resources.
The advent of hypertext-linked "web" technology combined with the global network of networks known as the INTERNET have made a wide variety of information of varying types and diverse forms available. Worldwide-web technology empowers individuals and organizations around the globe (and in space) with almost instant access to myriad sources of widely distributed information and information services. This technology, providing access to enormous quantities of data and multimedia information, has increasingly been incorporated into and supports the federal government's information infrastructure and national security processes. Whether national security operations and supporting services will be overloaded by the information or whether we control distribution of the information to provide knowledge needed for strategic and tactical advantage depends on development of sound information management practices and capabilities.
National security organizations and decision-makers throughout the world continue to face new, increasingly complex and short-fused challenges. For the national security organizations of our federal government to respond to these challenges requires first and foremost a commitment to understand them. Knowledge contributes to understanding and is gained to knowledge-based information.
Those engaged in the national security enterprise must be provided awareness and access to all information that contributes knowledge they need for effective decisions supporting national security operations. That knowledge-based information must be delivered to those needing it, where they need it, when they need it, in the sequence they need it, and in the format and context enabling its rapid assimilation by those to whom it is presented. But in establishing the policies, doctrine, processes, procedures and infrastructure to provide this information dissemination management (IDM) service, an adaptive posture and strategy must be enabled to facilitate rapid detection and response to unforeseen challenges that may emerge. In short, the larger challenge is to seize the opportunity to enable a more agile national security enterprise.
Out of a concern for the competitiveness of U.S. manufacturing in the global market, in 1991 the DOD commissioned a report, 21st Century Manufacturing Enterprise (Iacocca Institute), authored by Steven Goldman and Kenny Preiss of Lehigh University. The report described the concept of an agile enterprise, a key feature of which was the ability of an organization or group of organizations to fragment itself into smaller, leaner, more flexible groups of specialists able to reconfigure on demand to meet market needs and global competitive challenges.
The agile enterprise concept is based on the precept that business processes and procedures should serve the enterprise, and not the reverse. In order to remain competitive and viable in an increasingly competitive global environment, it is imperative for businesses (and national security organizations) to understand that they need to operate efficiently and effectively, providing those they serve with the products and services they need to carry out their missions and functions. A successful enterprise takes advantage of what the commercial marketplace has to offer. Those organizations that don't collaborate and don't form alliances will soon find themselves increasingly isolated. Therefore, our national security organizations must collaborate and interoperate across the broad spectrum of the federal government in order to provide the best information products and services on time, at the best price.
The agile enterprise concept is easily adaptable to the national security enterprise of our federal government. Just as the original agile enterprise concept focused on smaller, complementary, and reconfigurable areas of manufacturing expertise, an agile national security enterprise should be focused on a high degree of collaboration across components of the government to produce knowledge products on national security threats, readiness postures and operations. The ability to "reconfigure" national security resources on demand to meet the needs of operating commands involves, not only agility in adapting roles, relationships, missions and functions "on the spot" to meet current threats, but also agility in reconfiguring, interrelating, and integrating information resources to provide the knowledge needed for those operations. Even better, national security resources can be "reconfigured" in anticipation of demand to achieve even greater agility.
The more agile national security enterprise anticipated by JOINT VISION 2010 must manage information as a critical corporate resource and readily share it across the government and appropriate allies. If our federal government cannot provide the right information to the right people at the right time and in useful form and context, operating commands will suffer and be forced to seek other (often-unreliable) sources to obtain the knowledge required for their decisions and actions. In fact, with the breathtaking growth of the INTERNET and the quantity and quality of open source information becoming available, those engaged in national security planning and operations are already exploring these resources directly, in addition to assured information services and sources of the government. It is not a coincidence that CNN is a ubiquitous fixture in intelligence and operations centers of our operating units.
Joint Vision 2010 describes the need for "information superiority," defined as "the capability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary's ability to do the same." The need for information superiority is vital to our nation. An efficient and cost-effective way to ensure that we provide superior information will emerge from a more agile enterprise centered on skilled knowledge workers and collaboration among sources and users of information products and services. National security organizations require timely and accurate knowledge-based information; suppliers require feedback on the knowledge that decision-makers in operating units need so that high quality information contributing to that knowledge can be provided with utmost efficiency, cost-effectiveness, and assurity.
At times competition among information providers may even be encouraged as a means of continually improving diverse information resources and services. Value-added providers who do not keep their services up-to-date and relevant to customers needs, or who do not form strategic and ad-hoc collaborative alliances, may find demand for their information or services erode. Users must be empowered to exploit the most efficient and responsive sources of information and services. Providers should similarly be encouraged to form cooperatives to more synergistically support enterprise-wide user profiles of needed information. Together, they can most cost-effectively invest in improved information sources, technology, and expertise that prove mutually beneficial as they adapt their business or functional processes to capitalize on and exploit these improved resources.
However, a national security "information marketplace" must not become a "free market" independent of constraints, controls, or management. Common information will be needed by all, and should be provided from common prudently managed resources. Furthermore, cooperative planning and funding (or "subsidizing") is necessary to ensure that adequate information service is provided for all potential "hot spots" around the world, not just those areas that are current "best sellers."
Neither information management, nor its subordinate function, "information dissemination management"(IDM) are "systems," but rather capabilities enabling a cost-effective and efficient "marketplace" of information products and services from which needed national security information can be identified and delivered. The concept of information management provides a perspective or framework for thinking about information resource management and discovering the expertise, tools, techniques, policies, and procedures for managing information resources. To establish and maintain a healthy and productive information marketplace, the government must expedite progress in establishing shared telecommunications infrastructure, information processing (operating) environments and data/information management environments. Though great progress is being made toward these individually across the government, additional attention and resource commitment is needed to managing them together (as an enterprise) to better support delivery and presentation of timely knowledge-based information products.
Our national security enterprise of the 21st Century must adopt an open enterprise-wide culture of collaboration and information sharing. Policies, doctrine, practices, and incentives that will foster that vision, along with the supporting information technologies and communications infrastructure will be needed to make it a reality.
Joint Vision 2010 makes this very point: "...The unqualified importance of information will not change in 2010. What will differ is the increased access to information and improvements in the speed and accuracy of prioritizing and transferring data brought about by advances in technology. While the friction and fog of war can never be eliminated, new technology promises to mitigate their impact."
Information management does not necessarily imply having access to more information; to the contrary, it frequently means providing less but the right information that provides the knowledge needed, at the time, by the decision-maker. It also means providing superiors tools to manage and assimilate that information and apply it to improved performance of the recipient's missions and functions.
Information management is a term that can be applied broadly or narrowly. In the broadest sense, information management includes the full set of issues surrounding the timely acquisition, processing, organization, and presentation of information needed by operating units at all echelons and by supporting organizations for the mission at hand. The focus of information management is on the people, missions, quality, accuracy, timeliness, and utility of the information being managed, while the underlying information technology should be applied to enable it to work effectively and efficiently in supporting coherent information management policies, plans and procedures.
The tools and technologies needed for acquiring, analyzing, manipulating, storing, searching, retrieving, transmitting, publishing and presenting information are increasing in speed and capacity, and steadily decreasing in cost. Available communications bandwidth of fiber and wireless systems is dramatically improving the ability to rapidly share information among analysts, processing facilities and operating commands. Higher capacity multimedia networking technologies are rapidly emerging, making it easier to access national security information regardless of format or location.
Nevertheless, even with the expanding potential that technology provides to shower decision-makers and organizations with information, showering them with data or information must not be the government's goal. Instead, the federal government must develop and apply information management principles, policies, doctrine, techniques, and procedures to reduce the volume and increase the timeliness and quality of knowledge-based information delivered. A set of principles is proposed below to guide it toward an appropriate course. These principles reflect the thrusts of many initiatives of the public and private sectors to achieve the vision of providing knowledge, tailored to the needs of the mission and the customer. The target capabilities must involve an enterprise venture ... national security organizations of the federal government must agree to set out together on the journey toward JOINT VISION 2010 sharing fundamental tenets for the capabilities that must be established to achieve the goals identified.
Fundamental Information Management Tenets

Accepting the Challenge - Progress Underway
The breadth and scope of this challenge is increased information and information technology management and oversight at the most senior levels of federal government.
Recent enactments of public law and executive direction refocus information technology management to directly support strategic missions, to implement investment review processes that drive budget formulation, and to execute life-cycle management of information systems purchased with taxpayer dollars. The legislation and direction also requires a rethinking and restructuring of the way government functions are performed, before investing in information technology to support government missions and functions. The goal is to reengineer work processes and to optimize management of information that will eventually avoid cost growth while improving performance of missions and functions. Agencies are required to monitor performance to ensure the goal is being reached. Until it is reached, they will find individual processes and functions can not be synergistically interconnected to achieve the significant level of performance improvements needed to achieve JOINT VISION 2010.
Both the National Performance Review Report and subsequent Clinger-Cohen Act emphasized the importance of information management and exploiting information technologies to achieve national goals and objectives through prudent management of investments in information systems and process improvements.
The position of Chief Information Officer (CIO) was established for federal agencies by the Clinger/Cohen Act and CIOs are expected to ensure agencies implement the management principles dictated by the Law and, thereby, significantly improve the management and application of information resources to produce a government that works better for less.
Department of Defense Enterprise-Integration
The DOD has long targeted similar goals, earlier in this decade through a defense enterprise integration strategy. A keystone of that strategy was information management. Though some may argue whether the Defense Enterprise Integration Strategy was ever fully implemented, few would challenge the progress the Department made in achieving many of its objectives. The major components of the strategy were these.
DOD Enterprise Integration Strategy Components
A great deal was achieved through this strategy. It initially had very senior and broadbased support. Also, it had support of congressional oversight committees, who viewed it as a means to break rice bowls and promote economy. It achieved much it set out to. A good idea, at the right time, but changing incumbents to key leadership positions impeded follow-through focus on fully implementing the strategy.
A DOD Information Dissemination Management Capability
As with any enterprise, managing information of the national security enterprise requires alignment of information resources to the operational processes of organizations involved. Operational concepts are required clarifying the missions and functions performed, the operational facilities involved and temporal relationships of activities of those facilities in performing those functions to accomplish assigned missions.
During the Joint Warrior Interoperability Demonstration (JWID) in 1995, the concept of "operational threads" emerged as an approach to modeling these entities and processes. The figure below describes the essential components of the underlying model within which "operational threads" were oriented. It also suggests the process necessary to ensure the right information is delivered to the right time to the right place in the right sequence in the right format and context to support the "operational threads" being examined.
The first step must be to understand the functions of the various operational facilities involved in the mission and the data needed to perform them; then an understanding of the information needlines is essential to map the flow of information among those operational facilities; finally, an operational architecture must be derived to support those needlines by distributing information among nodes supporting those facilities using systems compliant with applicable standards, to ensure interoperability among them.
Only in the context of such a process can the flow of information across available information infrastructure be adequately understood to establish and coordinate the functions and services required to manage information dissemination among operational facilities and their supporting establishment.
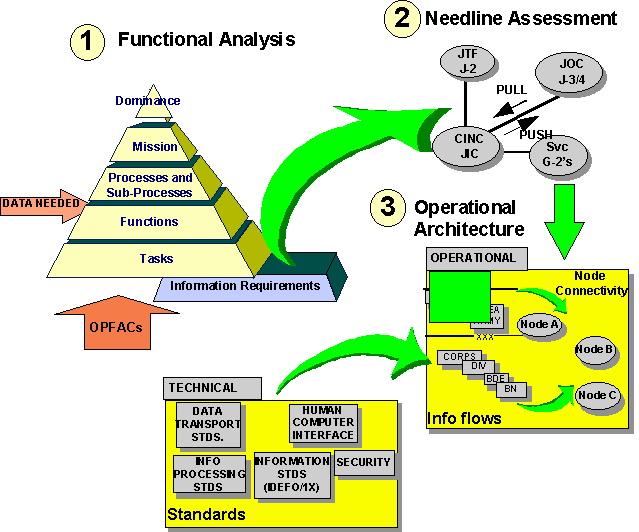
As indicated by the figure, JWID-95 also initiated the concept of "smart push and smart warrior pull" whereby some information is retrieved directly by those needing it while other information is sent (pushed) to them based on knowledge of others that they need it. This was a beginning of exploration of alternatives for information dissemination management (IDM). With the emergence of a global broadcast service to support operational units worldwide, these concepts and capabilities have become increasingly relevant.
An Information Dissemination Management Framework
As a basis for launching evolutionary improvements in enterprise-wide national security information management, IDM offers a most promising opportunity. Though information management involves many facets and dimensions, IDM offers a framework from which to orient management of information resources spanning all components of the enterprise, to improve awareness, access and delivery of information by information producers and users. IDM begins providing a means for DOD components to identify needed knowledge and enables an awareness of information products by potential users, making the information available to them and delivering it to the location its needed, when its needed, in the appropriate sequence, format, and context. In March 1998, the Acting ASD(C3I)promulgated an IDM Framework Document. The document was produced by an IDM Integrated Process Team (IPT) chartered by the ASD(C3I) Director of Communications a year earlier.
It established a common technical perspective of IDM functions and services and their interrelationships, initiating a broad strategy perspective on roles and relationships of DOD organizations in implementing a coherent and comprehensive IDM capability across the Department. Of particular importance is the element of the strategy that ensures implementation of IDM services as part of the DII Common Operating Environment (COE) and compliance with standards established by the DOD Joint Technical Architecture.
Pilot Early Operational Capability for IDM
The IDM Framework Document also initiated pilot IDM tools as an adjunct to GBS Phase II implementation, now underway.
Much progress is being made in promising pilot technology applications toward an early operational capability for IDM challenges associated with GBS operations. But, to achieve the potential benefits of enterprise-wide IDM, information transport management must extend composite network and data management of the combined GBS, DISN, and Service/agency networks. Coherent and comprehensive information dissemination management spanning all these resources is key to optimizing exploitation of the potentially powerful GBS information delivery services. Developing the management interfaces for both the terrestrial and space components of interconnected networks, establishing the interlinking management protocols, adapting all networks offer or efficiently interface with ATM-based information transport, and linking both network and data management is a complex challenge.
Nevertheless, a set of pilot emerging technology applications are being fielded to provide an early operational capability in USPACOM this year, with similar pilot applications planned for USACOM in the coming year. In addition, the Joint C4ISR Battle Center (JBC) is planning operational assessments next year for these capabilities to be the basis for multi-command recommendations for their improvements and adaptation. These assessments are expected to include new Joint Task Force perspectives on the needed IDM capability and recommendations regarding the impact of IDM applications on joint and coalition warfare.
However, to achieve the level of information dissemination management to be needed for Joint Vision 2010 objectives, much more is needed than exploration of applications of emerging technology.
A Formal IDM Requirement
These early experiences with IDM have enabled a better understanding of the potential benefits of a DOD-wide IDM capability toward achievement of Joint Vision 2010 objectives for information superiority in national security operations. As a result, the Joint Staff is now engaged in coordinating a mission need statement (MNS) to firmly establish the need for the capability. Once validated, the MNS will be the basis for a capstone joint operational requirements document (ORD) which can be used by the Joint Resource Oversight Council (JROC) to justify resource allocation decisions by the Joint Staff, Military Departments and Office of the Secretary of Defense to implement the needed capability. This should enable funded programs to be implemented in the coming decade to ensure operational readiness envisioned by Joint Vision 2010 to respond to threats anticipated in the new millennium.
An IDM Strategy for Achieving Joint Vision 2010
In anticipation of validation of the IDM MNS and approval of a DOD IDM ORD, an Intelligence Community initiative is already underway to produce a Community Action Plan for IDM. In addition, the Joint Staff is leading efforts of the Department to produce a DOD IDM Concept of Operations and Implementation Strategy to guide IDM program planning and implementation. A major component of the strategy is establishment of a DOD executive agency (EA) for IDM. The designated agency will act for the Office of the Secretary of Defense (OSD), Joint Staff, Military Departments, and Agencies represented on the Military Communications and Electronics Board (MCEB) in expediting planning and coordinating efforts across the DOD and other supporting organizations for implementing a DOD-wide IDM capability.
Critical to the strategy is acknowledgment that IDM cannot be achieved solely through technology solutions. The entire Department must cooperate in expediting evolutionary improvements in information management policies, doctrine, processes, tactics and procedures that are consistent with the capabilities to exploit powerful services of emerging information technologies. To succeed the entire DOD and Intelligence Community must cooperate in an evolutionary strategy to achieve the Joint Vision 2010 goal. Though roles and responsibilities of individual organizations must be acknowledged, the designated agency must be empowered with authority to coordinate individual efforts and strongly influence resource allocation decisions critical to their consistent accomplishment.
Recognizing the importance of prompt coordinated action across the DOD to maintain and focus momentum toward the goal, an agency ought to be designated immediately. Since DISA was a principal participant and technical advisor to the IDM IPT which produced the Framework Document and was designated for FY97 by PBD 706 to produce an end-end IDM plan for the GBS early operational capability pilot, DISA is best postured to assume this role. A decade ago, the DOD faced a similar decision on expanding the missions and functions of the DOD Communications Agency to include DOD information systems services across the DOD. Now, the decision confronting the Department is whether the missions and functions of the DOD Information Systems Agency ought to include coordination of DOD-wide information dissemination management services and functions. If not, the Department must empower another organization with the authority and resources needed.
In implementing the decision to assume this role, the designated executive agency must acknowledge that the challenges of information dissemination management extend far beyond systems engineering functions involved in the GBS IDM early operational capability pilot. Changes will be needed to expand and support information management services across the DOD Information Infrastructure (DII), as outlined by the IDM Framework and emerging MNS. Though IDM services and functions will require support from DII COE engineers and will impact DII shared data environment (SHADE) planning and engineering and that for DISN information transport services, a broader and higher-level perspective is necessary to guide the evolution of technology applications to process and procedural adaptations necessary. These must extend beyond the DII COE, DII SHADE and DISN to include systems of Military Departments, agencies and organizations of DOD and supporting Departments and commercial services. Evolutionary adaptations will be required to respond to policy and doctrinal changes identified by OSD and the Joint Staff. They will also be required to respond to dynamically expanding information dissemination requirements of the operating commands and their supporting establishment.
Near-term Strategy - Maintaining the Momentum
Pending a decision on a designated DOD IDM Executive Agency, the Joint Staff can be expected to continue its leadership role in expediting coordination across DOD of an IDM MNS and capstone joint ORD, as well as guidelines for an IDM Implementation Strategy. The Intelligence Community can be expected to coordinate its IDM Community Action Planning with the Joint Staff to ensure consistency among activities of that plan and the DOD strategy. Also, DISA's IDM PMO supporting IDM pilot applications for GBS can be expected to continue support to that important activity. The JBC is moving forward with its planning efforts to assess the pilot IDM tools and services associated with GBS deployment and recommend potential improvements to support multi-command operational requirements, joint task forces and joint warfare in general.
Finally, the DISA IDM PMO is continuing to prudently apply all resources made available to it by PBD 706 to support these related IDM initiatives, pending additional resources allocated to IDM based on JROC decisions. Particularly, DISA is providing all possible support to Joint Staff leadership in coordinating a DOD IDM MNS, ORD and Concept of Operations, pending designation of the DOD IDM Executive Agency.